28
Internet of Things
The Internet of things, or (IoT), which are sometimes in English, the Internet of things, both for this word can be used. generally refers to many things, included things in the environment that we connected to the internet, and can by applications available in the smart phone and tablet control and management. The Internet of things in simple language, communication, sensors and devices with a network through which can communicate with each other and with interaction. This concept can be simply the Association of a smartphone with the TV is, or the complexity of the monitoring infrastructure and urban traffic. Washing machine and fridge taken up ; can this network a lot of devices around us).
in the design of its architecture Auto-ID Center, Massachusetts Institute of Technology (MIT) also participated.
The Internet of things conceptually new in the world of technology and communications to come, but the phrase the Internet of things, etc., for the first time in 1999 by Kevin Ashton, was used, and a world described in which anything, including objects, said John, to his identity, Digital, have, and computers allow it to organize and manage. The internet, now all people are connected, but with the internet things, all things are connected. Of course, earlier Kevin Kelly, in the book of rules of the new economic era of networks (1998) the topic nodes little smart (such as sensors, opening and closing of the door) that the global network internet can be raised.
one of the easiest understood and the most an example that can be ran thermostat Nast. You use this thermostat can Mobile YOUR the temperature of your home control and one of the most interesting points is that this thermostat can time sleep and ... you learn and when you are asleep the temperature according to the temperature that you set. so no need to worry about that half the night, your home warm or cool. This thermostat all the night is awake!
the smart that by Samsung bought also sensors different to create a smart home at your disposal puts. With the use of these sensors can notice what personal enter your home or outside of it can be done even in case of drip water is also a report related to the leakage system, water get.
with the development and promotion of the tools available in the ecosystem, e.g. smart bracelet for physical activity you can as soon as sleep you., the TV and the lights off, or even ahead of most of them on the car at the specified time, the best route to get you to the destination by the vehicle of choice for put into place, etc. SMS to the person in front of the post. In scale, the macro of the system can be used to improve the activities of the urban, such as counting the number of empty spaces available in the parking lot or check the quality of water, cities, and the situation of traffic also benefited.
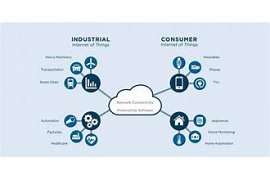
The Internet of things Industrial Internet of Things), or for stands for the IIOT is one of the most important and widely used field, the proliferation of the Internet of things. IIOT means the application of this technology in the industrial field and use it as a network industrial smart. With the use of the IIOT in industrial units can be all the objects in the IT unit are connected to each other ... and an integrated network to conduct all the affairs of the exchange of information, the conduct of control and monitoring.
This technology is among the 4 Big Tech in the main, which placed the future of industrial automation in the future heavily under the influence of the will. The progress of this technology, since that would be according to the predictions made by the year 2020, and with the arrival of the company, and enable automation to this field, the market value of this technology to over 319 billion dollars, that figure is significant, and worth the investment....