31
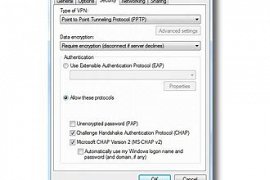
Point to Point Tunneling Protocol
Protocol PPTP is an acronym of Point to Point Tunneling Protocol is a form of protocol, peer-to-peer is that for communication the internet is used.
PPTP by Microsoft made up of virtual private networks support. This network, to entities and organizations allow the internet as a secure method to communicate information to use.
PPTP, from hidden storage package encrypted in the warpper, safe, supported through a TCP/IP connection, transfer find....