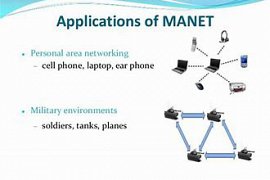
50
Peripheral Component Interconnect
Crossings in the computer wire that able data and commands with speed, from among the unit processor Central, ETC., memory and peripherals your computer, move said to be. Width to the number of bit data in a unit of time can pass. (8, 16 or 32 bit data) refers.
the PCI area of a card is grouped with the hand to connect making two or more holes help that in the BUS are placed in (from the tip to the floor, which include: X16 and X1 X16 X4), expressed that this area, as the gap from the know, and with a gap 32-bit PIC comparison. In the design of a computer, a bus is: a system of sub-data between the elements of the Inner a computer transfer. On the contrary, a Connect point-to-point, a bus logically can be several environments with a similar set of systems connected. Each bus collection connecting your equipment two branches, physical, cards or cables together define. bus, computers, the basic meaning of the literal bus, electrical, double-sided, with connections composite. but nowadays, this is the term for any regular collection of physical roles that a logical entity, such as a bus, electric bilateral. are applied. bus, a modern computer can connections bilateral connections with the serial number bit has used, and can be in one place trailing or location of the central processor, connected or the like box USB by Hub, locked connection ....