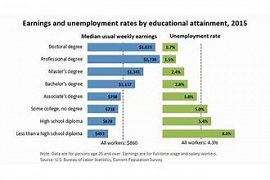
44
Operation Good Guys
OGG or OG A a container format file, a free and open source, which means the foundation Xiph.Org maintenance and development are given. The creators of the format OG Jay stated that this extension without the limitations of software patents is, and to provide the transfer (streaming) and effective manipulation of multi-media digital ([digital multimedia]) high quality design.
the template or within the content og a can be a number of streams independently for sound, images, text (such as subtitles), and metadata to combine together.
in the framework of multimedia OG). Theora, a video layer provides . Layers of sound, mainly by the form music axis, can be prepared, but other options include codec, speech compression, human or speaks, etc. codec compression, lossy sound, or Ferris and OG TV, Zune!.
before the 2007 extensions .ogg for all the files that are in the content they casted contain be used. After the 2007 Foundation Xiph.Org recommended that the extension .ogg only for audio files OG JAY be used. Foundation Xiph.Org decided a new set of file extensions and the type of media ( media types ) to describe the different types of content such as .oga just for audio files, etc..ogv for video with or without sound ( including Theora ), and .ogx for the OG, a compound create.
from 7 December 2007]. the current version of the reference implementation of the Xiph.org big liberal Democra OG Jay (libogg) version 1.2.2 . The other version of the. Liberal Democra OG Jay 2, etc. is expanding, but from 2008 waiting for the write retries. Both libraries software, free software, are under the authorization letter, SMS, new is published. Reference executive OG Jay on September 2, 2000 from was isolated.
from where this template is free, and its reference implementation is under the authority of the limits to copyright. codec various OG A a number of media players different free and proprietary, commercial and non-commercial, plus, player, media, portable, and receiver, GPS of different plant is used....